All about Nginx SSL ciphers
Essential information about SSL ciphers
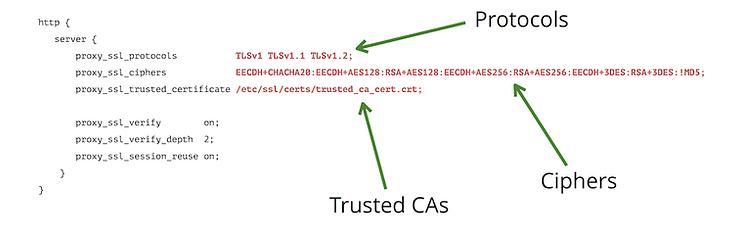
Nginx SSL ciphers are an essential component of securing websites with SSL/TLS encryption. SSL/TLS encryption is a protocol that ensures secure communication between a client and a server by encrypting the data transmitted over the internet. Nginx, a popular web server and reverse proxy server, provides a module that allows users to configure SSL/TLS encryption and choose the appropriate ciphers for their websites. Securing a website with SSL/TLS encryption is crucial for protecting sensitive information such as login credentials, credit card details, and personal data. Without encryption, this information can be intercepted and accessed by malicious actors. By implementing SSL/TLS encryption, website owners can ensure that their users’ data is protected and build trust with their audience.
Understanding SSL/TLS encryption and ciphers
SSL/TLS encryption is a cryptographic protocol that provides secure communication over the internet. It uses a combination of symmetric and asymmetric encryption algorithms to encrypt the data transmitted between a client (such as a web browser) and a server (such as a web server). The encryption process involves the exchange of digital certificates, which verify the identity of the server and establish a secure connection. SSL/TLS ciphers are algorithms used to encrypt and decrypt data during the SSL/TLS handshake process. These ciphers determine the strength of the encryption and the level of security provided. There are various types of ciphers, including symmetric ciphers (such as AES) and asymmetric ciphers (such as RSA). It is important to choose strong ciphers that provide robust encryption and protect against potential attacks. Choosing strong ciphers is crucial for ensuring the security of SSL/TLS encryption. Weak ciphers can be vulnerable to attacks such as brute force attacks, where an attacker tries all possible combinations to decrypt the encrypted data. By selecting strong ciphers, website owners can enhance the security of their websites and protect against potential threats.
How Nginx SSL ciphers work
Nginx provides a built-in SSL module that allows users to configure SSL/TLS encryption for their websites. This module handles the SSL/TLS handshake process, which includes the exchange of digital certificates and the negotiation of encryption algorithms and ciphers. To configure SSL/TLS encryption in Nginx, users need to specify the SSL parameters in the server block of the Nginx configuration file. These parameters include the SSL certificate and private key, the SSL protocols to be used, and the SSL ciphers to be enabled. Nginx supports a wide range of SSL ciphers, allowing users to choose the appropriate ones based on their security requirements. During the SSL/TLS handshake process, Nginx negotiates the encryption algorithms and ciphers with the client. It selects the strongest cipher that is supported by both the client and the server. Once the cipher is selected, Nginx uses it to encrypt and decrypt the data transmitted between the client and the server.
Best practices for configuring Nginx SSL ciphers
When configuring Nginx SSL ciphers, it is important to follow best practices to ensure the security of the SSL/TLS encryption. Here are some recommendations for configuring Nginx SSL ciphers:
Choosing strong SSL/TLS ciphers
Selecting strong ciphers is crucial for ensuring the security of SSL/TLS encryption. It is recommended to use ciphers that provide robust encryption and are resistant to potential attacks. Some commonly used strong ciphers include AES256-SHA256 and ECDHE-RSA-AES256-GCM-SHA384.
Disabling weak ciphers
Weak ciphers can be vulnerable to attacks and should be disabled to enhance the security of SSL/TLS encryption. It is recommended to disable ciphers that use outdated encryption algorithms or have known vulnerabilities. Examples of weak ciphers include DES-CBC3-SHA and RC4-MD5.
Configuring SSL protocols
SSL protocols determine the version of SSL/TLS encryption used for communication. It is important to configure Nginx to use the latest and most secure SSL protocols, such as TLS 1.2 or TLS 1.3. Older protocols, such as SSLv2 and SSLv3, should be disabled as they are known to have security vulnerabilities.
Setting up SSL certificates
SSL certificates are used to verify the identity of the server and establish a secure connection. It is important to obtain a valid SSL certificate from a trusted certificate authority (CA) and configure Nginx to use the certificate. This ensures that the communication between the client and the server is encrypted and secure.
Common SSL vulnerabilities and how to mitigate them with Nginx
SSL/TLS encryption is not immune to vulnerabilities, and it is important to be aware of common SSL vulnerabilities and how to mitigate them with Nginx. Here are some common SSL vulnerabilities and how Nginx can help mitigate them:
POODLE (Padding Oracle On Downgraded Legacy Encryption)
POODLE is a vulnerability that allows an attacker to decrypt encrypted data by exploiting a weakness in the SSLv3 protocol. To mitigate this vulnerability, Nginx users can disable SSLv3 and use more secure SSL protocols such as TLS 1.2 or TLS 1.3.
Heartbleed
Heartbleed is a vulnerability that allows an attacker to read sensitive information from the memory of a server or a client. Nginx users can mitigate this vulnerability by updating to the latest version of Nginx, which includes a fix for Heartbleed.
BEAST (Browser Exploit Against SSL/TLS)
BEAST is a vulnerability that allows an attacker to decrypt encrypted data by exploiting a weakness in the CBC (Cipher Block Chaining) mode of operation. To mitigate this vulnerability, Nginx users can enable TLS 1.1 or TLS 1.2, which use a different mode of operation that is not vulnerable to BEAST.
How to test your Nginx SSL cipher configuration
Testing your Nginx SSL cipher configuration is important to ensure that the SSL/TLS encryption is properly configured and secure. There are several SSL testing tools available that can help you test your SSL/TLS configuration with Nginx. One popular SSL testing tool is Qualys SSL Labs’ SSL Server Test. This tool allows you to scan your website and provides a detailed report on the SSL/TLS configuration, including the supported protocols, ciphers, and vulnerabilities. It also assigns a grade to your SSL/TLS configuration based on its security level. To test your Nginx SSL cipher configuration with Qualys SSL Labs’ SSL Server Test, simply enter your website’s URL in the provided field and click on the “Submit” button. The tool will then scan your website and provide a detailed report on the SSL/TLS configuration. When interpreting the SSL test results, it is important to look for any vulnerabilities or weaknesses in the SSL/TLS configuration. If any vulnerabilities are detected, you should take the necessary steps to mitigate them by updating your Nginx configuration and enabling stronger ciphers.
Nginx SSL cipher suites: which ones to use and which ones to avoid
SSL cipher suites are combinations of encryption algorithms and key exchange algorithms used during the SSL/TLS handshake process. There are various SSL cipher suites available, each providing different levels of security and compatibility. When choosing SSL cipher suites for Nginx, it is important to select strong cipher suites that provide robust encryption and protect against potential attacks. Some commonly recommended SSL cipher suites include:
ECDHE-RSA-AES256-GCM-SHA384
This cipher suite uses the Elliptic Curve Diffie-Hellman Ephemeral (ECDHE) key exchange algorithm and the Advanced Encryption Standard (AES) with a 256-bit key in Galois/Counter Mode (GCM). It provides strong encryption and is resistant to attacks.
DHE-RSA-AES256-GCM-SHA384
This cipher suite uses the Diffie-Hellman Ephemeral (DHE) key exchange algorithm and the AES with a 256-bit key in GCM. It provides strong encryption and is suitable for servers that do not support ECDHE.
ECDHE-RSA-AES256-SHA384
This cipher suite uses the ECDHE key exchange algorithm and the AES with a 256-bit key in Cipher Block Chaining (CBC) mode. It provides strong encryption and is compatible with a wide range of clients.
On the other hand, there are some SSL cipher suites that should be avoided due to their weak encryption or known vulnerabilities. Some examples of weak SSL cipher suites include:
DES-CBC3-SHA
This cipher suite uses the Data Encryption Standard (DES) with a 168-bit key in CBC mode. It provides weak encryption and is vulnerable to attacks.
RC4-MD5
This cipher suite uses the RC4 stream cipher with a 128-bit key and the MD5 hash function. It provides weak encryption and is vulnerable to attacks.
How to enable perfect forward secrecy with Nginx SSL ciphers
Perfect Forward Secrecy (PFS) is a property of SSL/TLS encryption that ensures that even if the private key of the server is compromised, past communications cannot be decrypted. This provides an additional layer of security and protects against potential attacks. To enable PFS with Nginx SSL ciphers, you need to configure Nginx to use Diffie-Hellman (DH) parameters. Diffie-Hellman is a key exchange algorithm that allows the client and the server to generate a shared secret key without transmitting it over the network. To generate DH parameters, you can use the OpenSSL command-line tool. First, generate a DH parameter file by running the following command:
openssl dhparam -out dhparams.pem 2048
This will generate a DH parameter file named “dhparams.pem” with a key size of 2048 bits. Once you have generated the DH parameter file, you can configure Nginx to use it by adding the following line to your Nginx configuration:
ssl_dhparam /path/to/dhparams.pem;
By enabling PFS with Nginx SSL ciphers, you can enhance the security of your SSL/TLS encryption and protect against potential attacks.
Troubleshooting Nginx SSL cipher issues
While configuring Nginx SSL ciphers, you may encounter some common SSL/TLS issues. Here are some common SSL/TLS issues with Nginx and tips for troubleshooting them:
Invalid SSL certificate
If you receive an error message indicating that the SSL certificate is invalid, you should check if the certificate is properly installed and configured in Nginx. Make sure that the certificate file and the private key file are correctly specified in the Nginx configuration.
SSL handshake failure
If the SSL handshake fails, it may indicate a compatibility issue between the client and the server. Check if the client supports the SSL protocols and ciphers configured in Nginx. You may need to adjust the SSL protocols and ciphers to ensure compatibility.
Mixed content warnings
If you receive mixed content warnings in your browser, it means that your website contains both secure (HTTPS) and insecure (HTTP) content. Make sure that all resources (such as images, scripts, and stylesheets) are loaded over HTTPS to avoid mixed content warnings. If you encounter any SSL/TLS issues with Nginx, it is recommended to consult the Nginx documentation or seek assistance from the Nginx community. They can provide guidance and solutions to resolve the issues and ensure the proper functioning of SSL/TLS encryption.
Conclusion: securing your website with Nginx SSL ciphers
Securing your website with Nginx SSL ciphers is crucial for protecting sensitive information and building trust with your audience. By implementing SSL/TLS encryption and choosing strong ciphers, you can ensure that the communication between your website and your users is encrypted and secure. In this article, we have discussed the importance of securing websites with SSL/TLS encryption and provided an overview of Nginx SSL ciphers. We have explained how SSL/TLS encryption works, how Nginx handles SSL/TLS encryption, and best practices for configuring Nginx SSL ciphers. We have also discussed common SSL vulnerabilities and how to mitigate them with Nginx, as well as how to test your Nginx SSL cipher configuration. Additionally, we have provided recommendations for choosing SSL cipher suites, enabling perfect forward secrecy, and troubleshooting SSL/TLS issues with Nginx. By following these guidelines and best practices, you can ensure the security of your website and protect against potential threats. Remember to regularly update your Nginx configuration and stay informed about the latest security updates and vulnerabilities.
